

ServiceNow Security Operations integrates incident data from your security products into a structured response engine that prioritizes and resolves risks based on their impact on your business, using intelligent workflows, automation, and a deep connection with IT.
Realize the full potential of your Now Platform® solution with Security Operations. Many businesses struggle to identify security threats and vulnerabilities, prioritize them, and work with IT to address them. Security analysts and vulnerability managers may use Security Operations to automate their security tools and interact with IT in a unified platform.

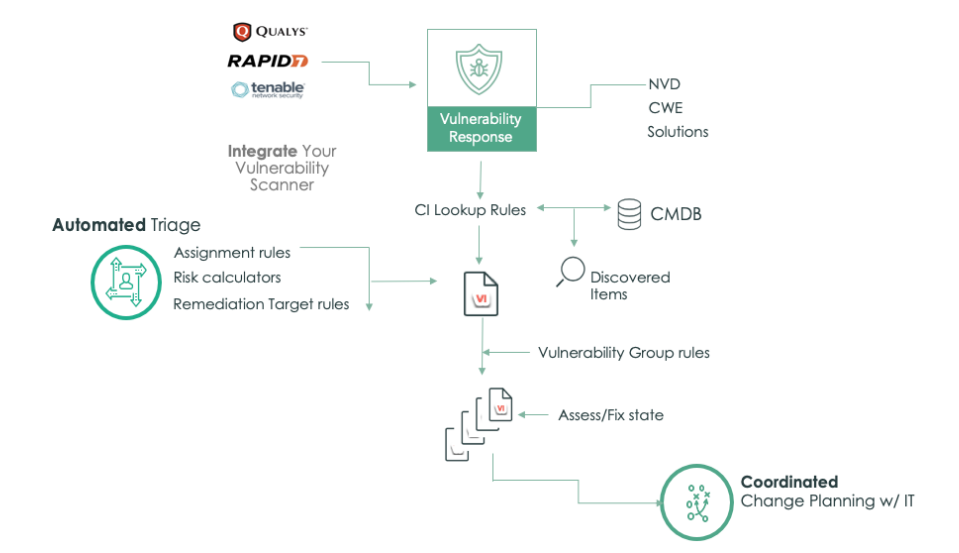
The Vulnerability Response application imports vulnerable items and automatically organizes them into groups based on group rules, allowing you to quickly fix vulnerabilities. Internal and external sources, such as the National Vulnerability Database (NVD) or third-party integrations, are used to gather vulnerability data. Vulnerability data from internal and external sources are extracted. Create change requests and security incidents for any vulnerable items, and use vulnerability groups to fix issues and minimize the risks.
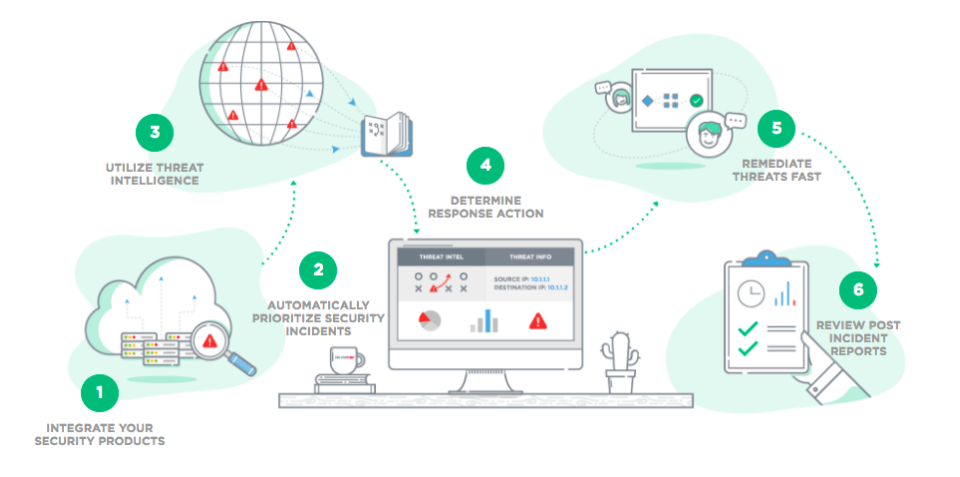
Integrate your existing Security Information and Event Manager (SIEM) tools with Security Operations apps using the Security Incident Response (SIR) application to integrate threat data (through APIs or email alerts) and automatically produce prioritized security incidents. Manage the period of your security events from primary analysis to eradication, containment, and recovery. With analytics-driven dashboards and reporting, the Security Incident Response app allows you to gain full knowledge of incident response procedures conducted by your analysts, as well as analyze patterns and bottlenecks in those procedures.
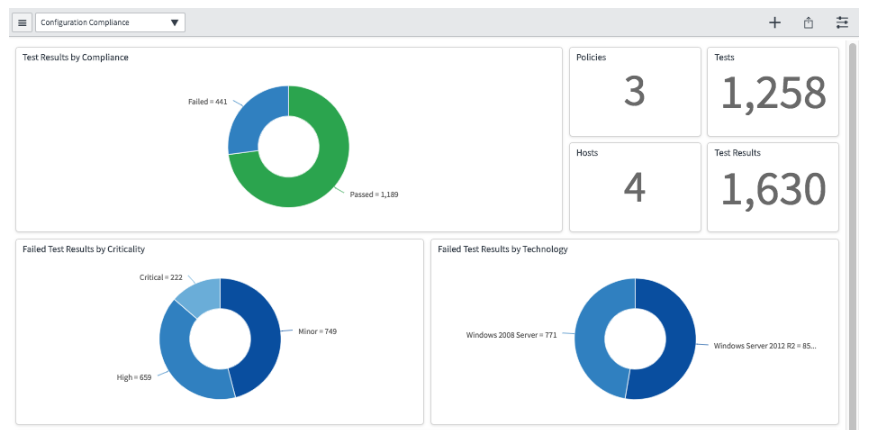
Use test results from third-party Strong Customer Authentication (SCA) integrations to check compliance with security or business standards using the Configuration Compliance application. The assets included in the ServiceNow® Configuration Management Database (CMDB) are used to identify which objects are the most essential in this application. Workflows and automation allow us to make bulk changes to individual assets or groups of assets fast. Identify and fix any configuration elements that aren't in compliance. Import policies, tests, authoritative sources, and technologies automatically, and assign test results to people or groups for remediation.
When an IoC is connected to a security incident, use the Threat Intelligence application to automatically scan threat feeds for relevant information and submit IoCs to third-party sources for further research. Structured Threat Information Expression (STIX) is a language used by the Threat Intelligence program to express cyber threat information in a consistent and structured manner.

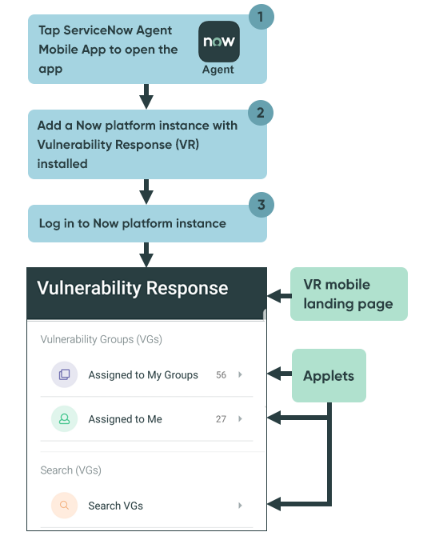
With your Android or iOS mobile device, access the Vulnerability Response and Security Incident Response applications on your Now Platform instance.
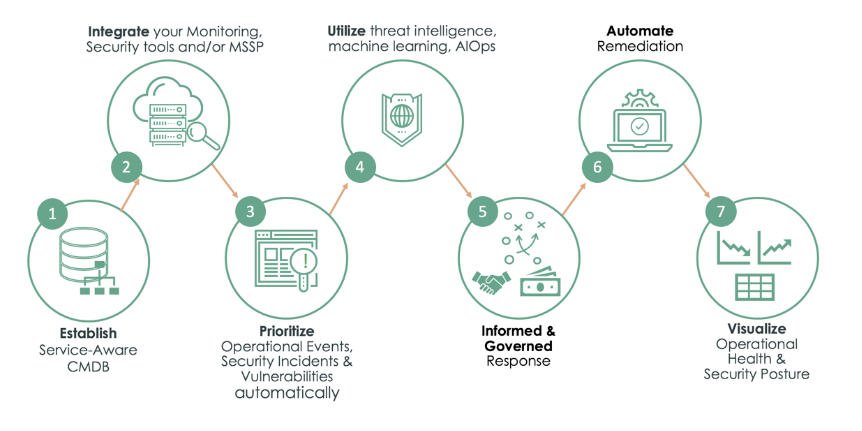
Security Operations integrates incident data from your security products into a structured response engine that prioritizes and resolves risks based on their impact on your business, using intelligent processes, automation, and a close relationship with IT.
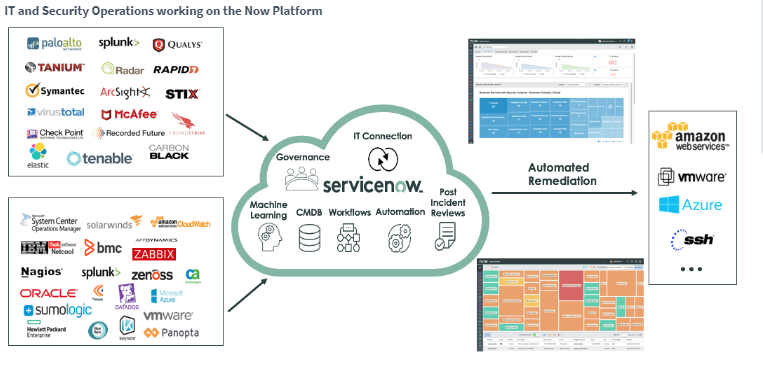
The Security Operations environment can be built in several ways, depending on the company's requirement and the Security Operations tools you permit. The flow of a basic Security Operations system is illustrated in the diagram below.
By working on a single platform, security analysts and vulnerability managers may interact with IT seamlessly. Patching and other duties may be delegated to IT while keeping visibility into the process. Tasks are assigned to the appropriate responders based on their skills, and service level agreements guarantee that the work is completed on time. The ServiceNow Program expedites more agile collaboration among security and IT workers; however, sensitive security data is secured by user roles. It implies that people with the admin role can't access security data unless they also have the security role.
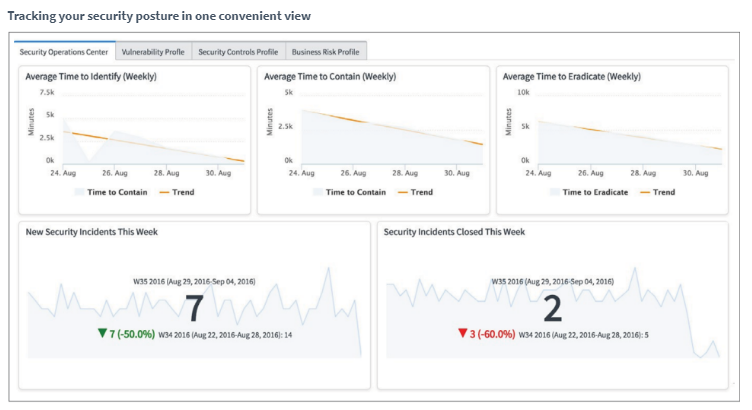
Security Operations allows role-based reports and dashboards you can customize to display the state of your security. All security events and vulnerabilities are graphically shown, together with additional context, to demonstrate how threats are influencing your essential business services. Dashboards improved with ServiceNow Performance Analytics display the state of your security overall performance, allowing you to monitor how your security posture is developing.
Security Operations apps use the Now Platform's capability to scale your security solution to your business's requirements and the sorts of cyber threats you face.
Security Operations appears to be a riddle, as illus1trated. The power and flexibility of the Now Platform become obvious when the parts are put together and the picture is revealed. In the next sections, each application, as well as the other applications that each contact, is detailed.
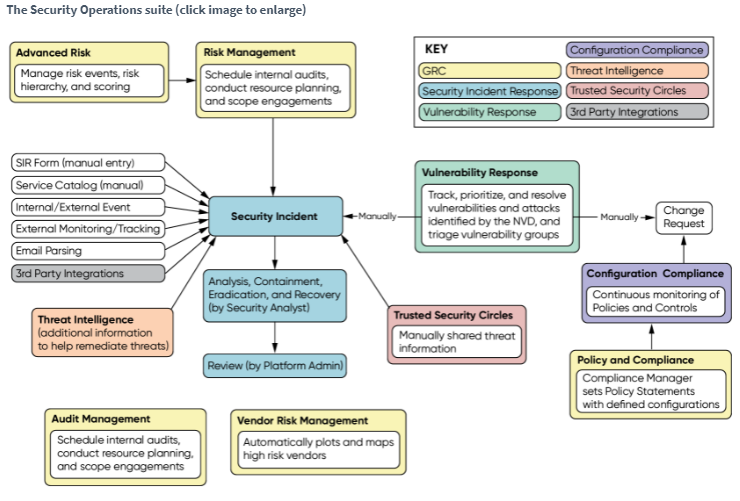
The Security Incident Response (SIR) app is at the center of the Security, Operations ecosystem. Security Incident Response streamlines the process of detecting critical incidents by using strong workflow and automation capabilities. There are several ways to create security incidents both automatically and manually inside the Security Operations ecosystem. Response tasks may be convenient to viewed and tracked. If tasks are not performed on time, Security Incident Response alerts analysts assigned to them, or the tasks are automatically elevated, depending on how the system is set up. As a result, no activities are neglected, or decisions are ignored. Analysts may also use the Now Platform to keep stakeholders informed by holding conference calls or using the Connect chat tool. When Security Incident Response is connected with the ServiceNow Threat Intelligence platform, it automates simple activities like authorization requests, malware scans, and threat data enrichment. This type of automation allows the security team to spend more time hunting complex and critical threats while also speeding up incident response. From within Security Operations, orchestration packs for integrated security products automate frequently repeated actions, such as firewall block requests. Playbooks allow you to take a step-by-step approach to resolve specific sorts of security risks. Playbooks, for example, can be used to resolve phishing attempts and threats generated by malicious code activity. The platform keeps track of all incident actions, from analysis and research through containment and cleanup. When an incident is resolved, all team members receive a post-event evaluation, which serves as a historical audit record for future reference.
The Vulnerability Response application helps you prioritize your susceptible assets and provides context to assist you to identify when business-critical systems are at risk. Vulnerability Response may also rapidly detect cross-system dependencies and analyze the business effect of changes or downtimes by using the CMDB. You can see all the vulnerabilities that affect a certain service as well as the current condition of all the vulnerabilities that affect your company. To fix vulnerabilities faster, response teams can use the Now Platform's workflow and automation features. A process can automatically launch an emergency patch approval request when serious vulnerabilities are discovered. Once the patch has been authorized, orchestration tools may install it and run another vulnerability check to confirm the problem has been fixed. Simply click a button to generate a change request and transmit the appropriate information to IT for non-urgent updates. As a consequence, a coordinated vulnerability remediation strategy for services and assets is created, allowing the essential elements to be addressed promptly.
A threat intelligence application is included in Security Operations to assist incident responders in locating Indicators of Compromise (IoC) and hunting for low-level assaults and threats. When an IoC is linked to a security event, it automatically scans threat feeds for relevant information and can send IoCs to third-party sources for further research. The results are directly recorded in the security incident record for evaluation by the analyst, saving time. To include threat intelligence data from several sources, ServiceNow supports various threat feeds, as well as STIX and TAXII.
Organizations are at threat of being hacked if the software is installed inappropriately. Configuration Compliance uses data from third-party security configuration assessment scans to prioritize and fix misconfigured assets. It uses the CMDB to figure out which things are the most important. Workflows and automation allow us to make bulk changes to individual assets or groups of assets efficiently. To address changes and upgrades, easily collaborate with IT on a single platform. Configuration Compliance data may also be provided into ServiceNow Governance, Risk, and Compliance's continuous monitoring capability to help minimize risk.
With Trusted Security Circle, you may share threat intelligence data with industry colleagues, suppliers, or a worldwide circle of ServiceNow customers. Send an anonymous query to other users including security observables, and get automated sightings to count. Security analysts can use this information to see if the unusual activity is part of a wider assault. If the observable count limit is surpassed, users can define sightings count thresholds to automatically initiate a security issue. Participating in the Trusted Security Circle can act as an early warning system for attacks aimed at certain organizations.
The ServiceNow Governance, Risk, and Compliance (GRC) apps aid in the transformation of inefficient procedures throughout your extended business into a comprehensive risk management program. ServiceNow provides a real-time picture of compliance and risk, enhances decision making, and improves performance across your business and with vendors through continuous monitoring and automation.
How the Governance, Risk, and Compliance applications work with Security Operations applications (click image to enlarge)
Every beautiful relationship starts with a simple hello. So let’s chat. It might just be the start of something memorable.

